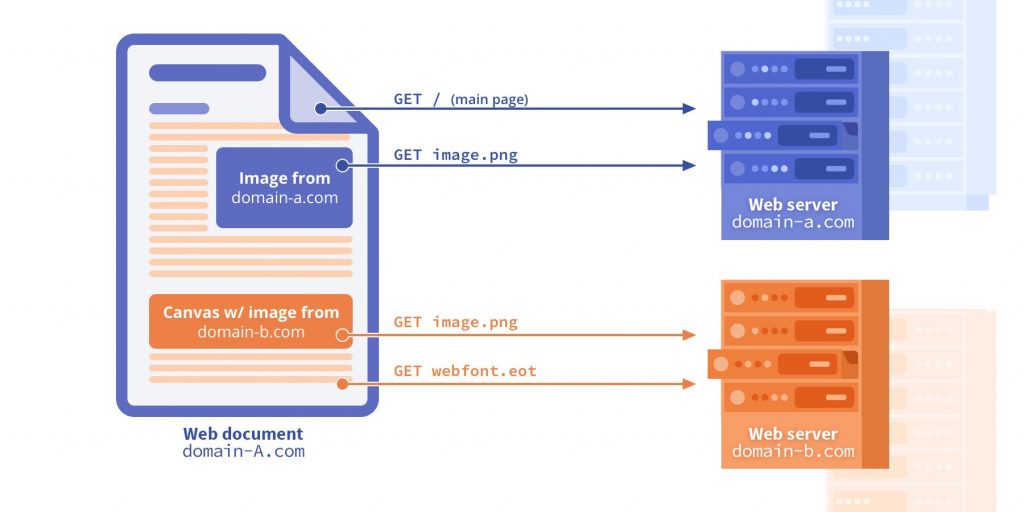
When a script on one server sends an Ajax request to another, this is referred to as cross-origin resource sharing (CORS). Cross-origin resource sharing also occurs when a request is sent to the same server using a different protocol or port.
The 'same origin policy,' which is in place to prevent cross-site request forgery attacks, is violated by cross-origin resource sharing. While global cookie prevention for /api/* endpoints prevents these attacks, browsers continue to try to enforce this policy. This convention is followed by all browsers, but it does not apply to manual request mechanisms such as cURL.
Browsers detect that you are attempting to make a server request and send a preflight request. Preflight requests are configured as OPTION requests against the same URL, but they also include the Origin header. Other information such as allowed request types, whether to expect headers in the response to the actual request, and whether the origin is accepted must be returned by the server.
The browser rejects the preflight request if the 'Access-Control-Allow-Origin' header of the response does not match the Origin header of the request. If the 'Access-Control-Allow-Origin' header is present, the browser will process the request. If the rule changes between the preflight and actual request, the request's response must pass the same origin check.

Management of permitted origins
The protocol is followed by the host name and port in the origin value sent by your browser, for example:
http://192.0.2.0:8888
You can intercept browser requests to ensure that you have the correct origin value. On the QRadar® Console, you can whitelist your origin in the /opt/qradar/webapps/console/restapi/allowed origins.list file. Changes are detected and immediately implemented. This file contains a list of allowed origins separated by newlines. Each entry is validated against the origin header that browsers send during pre-flight requests. If an entry matches the origin (or if any entry is '*,' the browser is permitted to make cross-origin resource sharing requests.
By adding '*' to the whitelist, a common browser convention is to send null as the origin when the script is started from file:/. This is a bad practice because it allows all origins.