Introduction
In today's interconnected world, the web is a hub of information and services that seamlessly communicate with each other. However, due to security concerns, web browsers enforce strict policies that limit resource sharing between different origins. To enable controlled data sharing, Cross-Origin Resource Sharing (CORS) emerged as a vital mechanism. In this blog post, we will delve into the world of CORS, understanding its purpose, how it works, and its significance in fostering secure and collaborative web experiences.
What is Cross-Origin Resource Sharing (CORS)?
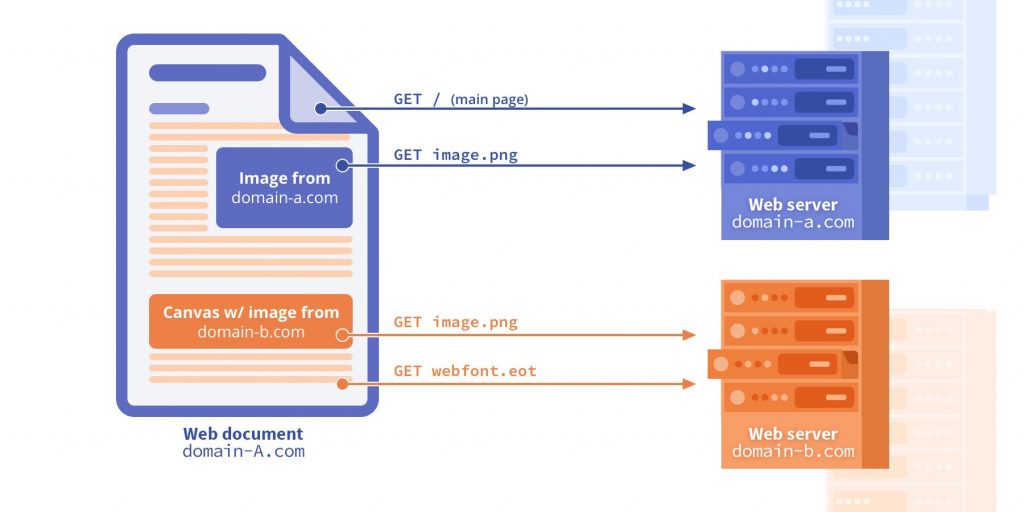
Cross-Origin Resource Sharing, commonly known as CORS, is a web standard that allows web applications running on different domains to request and share resources with each other. By default, web browsers apply the Same-Origin Policy (SOP), which restricts resource sharing between different origins (schemes, domains, and ports) to mitigate cross-site scripting (XSS) attacks. CORS acts as a gatekeeper, permitting selective cross-origin requests while maintaining security.
The Need for CORS
In the early days of the web, applications were predominantly standalone and accessed resources solely from the same domain. However, as web applications evolved, the need for cross-origin communication became evident. Consider a scenario where a frontend application hosted on domain A needs to fetch data from an API hosted on domain B. Without CORS, the web browser would block such requests, thwarting collaboration and hindering the modern web's potential.
How Does CORS Work?
CORS operates through a series of HTTP headers exchanged between the client (web browser) and the server. When a web page sends a cross-origin request, the browser attaches an "Origin" header containing the requesting domain's information. The server, upon receiving the request, evaluates this header to determine whether it is safe to share resources. The server responds with appropriate CORS headers to allow or deny the request based on predefined rules.
CORS Headers and Their Purpose
1. Access-Control-Allow-Origin: This header specifies which origins are allowed to access the resource. It can be a specific domain, "*", indicating any origin, or null when no origins are permitted.
2. Access-Control-Allow-Methods: This header defines the HTTP methods (e.g., GET, POST, PUT, DELETE) allowed for cross-origin requests.
3. Access-Control-Allow-Headers: It specifies the headers that the server permits in the actual request.
4. Access-Control-Expose-Headers: This header lists the response headers that the client can access.
5. Access-Control-Allow-Credentials: When set to "true," it indicates that the server allows credentials (e.g., cookies, HTTP authentication) to be included in cross-origin requests.
Benefits of CORS
1. Enhanced Web Security: By adhering to the SOP and employing CORS, browsers can ensure that malicious scripts from one domain do not access resources from another domain, effectively mitigating XSS attacks.
2. Collaborative Web Applications: CORS enables web applications to fetch resources, such as APIs or assets, from different domains, facilitating collaboration and integration among various services and domains.
3. Granular Control: CORS allows server administrators to specify which domains are permitted to access resources, providing fine-grained control over cross-origin requests.
4. Seamless Cross-Domain Communication: With CORS, developers can build powerful web applications that interact with multiple APIs and services hosted on different domains, creating more dynamic and interactive user experiences.
Common CORS Pitfalls
1. Misconfiguration: Incorrectly configuring CORS headers can lead to unintended consequences, either blocking legitimate requests or allowing unauthorized access. Proper configuration and testing are crucial.
2. Security Vulnerabilities: CORS headers must be carefully designed to prevent unauthorized access to sensitive information. For instance, allowing the "Access-Control-Allow-Origin" header to include "*" could expose data to unintended origins, increasing the risk of data leakage or unauthorized access.
3. Lack of Browser Support: While CORS is widely supported by modern web browsers, some older or less common browsers may not fully support it. It is essential to consider browser compatibility when implementing CORS in web applications.
Best Practices for Implementing CORS
1. Understand Your Application's Requirements: Determine which resources need to be shared across origins and define the appropriate CORS policies accordingly. Consider the sensitivity of the data being accessed and design CORS headers with security in mind.
2. Configure CORS Headers Correctly: Ensure that the "Access-Control-Allow-Origin" header is set to a specific domain or a limited set of trusted domains rather than using "*" as a wildcard. This reduces the risk of unauthorized access to sensitive data.
3. Limit Exposed Headers: Only expose the necessary response headers through the "Access-Control-Expose-Headers" header. Minimizing the number of exposed headers helps protect sensitive information from potential attackers.
4. Use Appropriate HTTP Methods: Set the "Access-Control-Allow-Methods" header to allow only the necessary HTTP methods required for cross-origin requests. Restricting unnecessary methods reduces the attack surface and enhances security.
5. Enable Credentials Sparingly: Use the "Access-Control-Allow-Credentials" header judiciously, enabling it only when necessary. Enabling credentials in cross-origin requests poses additional security risks, so consider the implications before allowing them.
6. Test and Validate CORS Configuration: Thoroughly test and validate the CORS configuration of your web application to ensure that resources are shared securely across origins. Verify that only intended domains can access the resources and that no sensitive data is exposed inadvertently.
Conclusion
Cross-Origin Resource Sharing (CORS) plays a pivotal role in enabling secure collaboration and resource sharing across different domains on the web. By facilitating controlled cross-origin requests, CORS enhances web security while allowing developers to build dynamic and interactive applications that leverage resources from various origins. However, proper configuration and careful consideration of security implications are crucial to ensure that CORS is implemented correctly. With a solid understanding of CORS and adherence to best practices, developers can harness its power to create robust and collaborative web experiences.